[ad_1]
Organizations within the throes of cleansing up after a ransomware outbreak sometimes will change passwords for all person accounts which have entry to any e mail programs, servers and desktop workstations inside their community. However all too usually, ransomware victims fail to understand that the crooks behind these assaults can and continuously do siphon each single password saved on every contaminated endpoint. The results of this oversight might supply attackers a manner again into the affected group, entry to monetary and healthcare accounts, or — worse but — key instruments for attacking the sufferer’s varied enterprise companions and purchasers.
In mid-November 2019, Wisconsin-based Digital Care Supplier Inc. (VCPI) was hit by the Ryuk ransomware pressure. VCPI manages the IT programs for some 110 purchasers that serve roughly 2,400 nursing properties in 45 U.S. states. VCPI declined to pay the multi-million greenback ransom demanded by their extortionists, and the assault minimize off a lot of these elder care amenities from their affected person data, e mail and phone service for days or perhaps weeks whereas VCPI rebuilt its community.
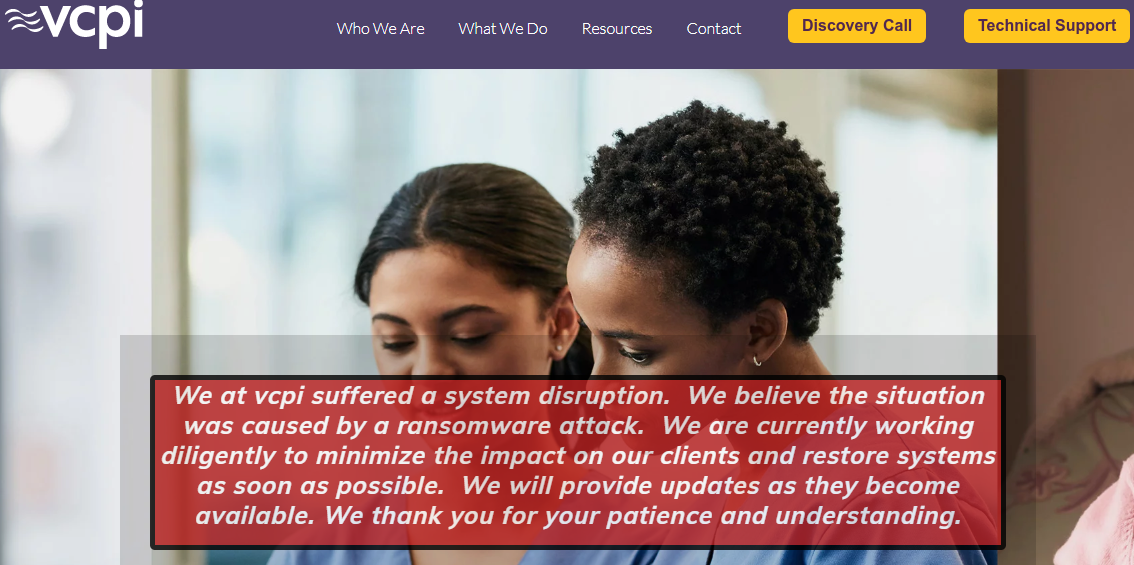
Simply hours after that story was revealed, VCPI chief govt and proprietor Karen Christianson reached out to say she hoped I might write a follow-up piece about how they recovered from the incident. My reply was that I’d take into account doing so if there was one thing of their expertise that I believed others may be taught from their dealing with of the incident.
I had no inkling on the time of how a lot I might be taught within the days forward.
EERIE EMAILS
On December three, I contacted Christianson to schedule a follow-up interview for the following day. On the morning of Dec. four (lower than two hours earlier than my scheduled name with VCPI and greater than two weeks after the beginning of their ransomware assault) I heard by way of e mail from somebody claiming to be a part of the felony group that launched the Ryuk ransomware inside VCPI.
That e mail was unsettling as a result of its timing prompt that whoever despatched it one way or the other knew I used to be going to talk with VCPI later that day. This particular person mentioned they wished me to reiterate a message they’d simply despatched to the proprietor of VCPI stating that their supply of a tremendously lowered worth for a digital key wanted to unlock servers and workstations seized by the malware would expire quickly if the corporate continued to disregard them.
“Perhaps you chat to them lets see if that works,” the e-mail prompt.
The nameless particular person behind that communication declined to offer proof that they had been a part of the group that held VPCI’s community for ransom, and after an more and more combative and personally threatening change of messages quickly stopped responding to requests for extra info.
“We had been bitten with releasing proof earlier than therefore now we have stopped this even in our ransoms,” the nameless particular person wrote. “If you need proof now we have hacked T-Techniques as nicely. Chances are you’ll affirm this with them. We havent [sic] seen any Media articles on this and as such you need to be the primary to report it, we’re positive they’re simply protecting it beneath wraps.” Safety information website Bleeping Pc reported on the T-Techniques Ryuk ransomware assault on Dec. three.
In our Dec. four interview, VCPI’s performing chief info safety officer — Mark Schafer, CISO at Wisconsin-based SVA Consulting — confirmed that the corporate obtained a virtually similar message that very same morning, and that the wording appeared “very related” to the unique extortion demand the corporate obtained.
Nevertheless, Schafer assured me that VCPI had certainly rebuilt its e mail community following the intrusion and strictly used a third-party service to debate remediation efforts and different delicate subjects.
‘LIKE A COMPANY BATTLING A COUNTRY’
Christianson mentioned a number of components stopped the painful Ryuk ransomware assault from morphing right into a company-ending occasion. For starters, she mentioned, an worker noticed suspicious exercise on their community within the early morning hours of Saturday, Nov. 16. She mentioned that worker then instantly alerted higher-ups inside VCPI, who ordered a whole and rapid shutdown of all the community.
“The underside line is at 2 a.m. on a Saturday, it was nonetheless a human being who noticed a bunch of lights and had sufficient presence of thoughts to say another person may need to check out this,” she mentioned. “The opposite man he referred to as mentioned he didn’t prefer it both and referred to as the [chief information officer] at 2:30 a.m., who picked up his cellphone and mentioned shut it off from the Web.”
Schafer mentioned one other mitigating issue was that VCPI had contracted with a third-party roughly six months previous to the assault to determine off-site knowledge backups that weren’t immediately related to the corporate’s infrastructure.
“The authentication for that was solely separate, so the lateral motion [of the intruders] didn’t enable them to the touch that,” Schafer mentioned.
Schafer mentioned the transfer to third-party knowledge backups coincided with a complete inner overview that recognized a number of areas the place VCPI may harden its safety, however that the assault hit earlier than the corporate may full work on a few of these motion gadgets.
“We did a danger evaluation which was just about spot-on, we simply wanted extra time to work on it earlier than we bought hit,” he mentioned. “We had been doing the proper issues, simply not quick sufficient. If we’d had extra time to organize, it will have gone higher. I really feel like we had been an organization battling a rustic. It’s not a good struggle, and when you’re focused it’s fairly powerful to defend.”
WHOLESALE PASSWORD THEFT
Simply after receiving a tip from a reader in regards to the ongoing Ryuk infestation at VCPI, KrebsOnSecurity contacted Milwaukee-based Maintain Safety to see if its proprietor Alex Holden had any extra details about the assault. Holden and his staff had beforehand intercepted on-line site visitors between and amongst a number of ransomware gangs and their victims, and I used to be curious to know if that held true within the VCPI assault as nicely.
Certain sufficient, Holden shortly despatched over a number of logs of knowledge suggesting the attackers had breached VCPI’s community on a number of events over the earlier 14 months.
“Whereas it’s clear that the preliminary breach occurred 14 months in the past, the escalation of the compromise didn’t begin till round November 15th of this yr,” Holden mentioned on the time. “After we checked out this on reflection, throughout these three days the cybercriminals slowly compromised all the community, disabling antivirus, operating custom-made scripts, and deploying ransomware. They didn’t even succeed at first, however they saved attempting.”
Holden mentioned it seems the intruders laid the groundwork for the VPCI utilizing Emotet, a strong malware device sometimes disseminated by way of spam.
“Emotet continues to be among the many most expensive and harmful malware,” reads a July 2018 alert on the malware from the U.S. Division of Homeland Safety. “Its worm-like options lead to quickly spreading network-wide an infection, that are tough to fight.”
In line with Holden, after utilizing Emotet to prime VCPI’s servers and endpoints for the ransomware assault, the intruders deployed a module of Emotet referred to as Trickbot, which is a banking trojan usually used to obtain different malware and harvest passwords from contaminated programs.
Certainly, Holden shared data of communications from VCPI’s tormentors suggesting they’d unleashed Trickbot to steal passwords from contaminated VCPI endpoints that the corporate used to log in at greater than 300 Web pages and companies, together with:
-Id and password administration platforms Auth0 and LastPass
-A number of private and enterprise banking portals;
-Microsoft Workplace365 accounts
-Direct deposit and Medicaid billing portals
-Cloud-based medical insurance administration portals
-Quite a few on-line fee processing companies
-Cloud-based payroll administration companies
-Prescription administration companies
-Business telephone, Web and energy companies
-Medical provide companies
-State and native authorities aggressive bidding portals
-On-line content material distribution networks
-Transport and postage accounts
-Amazon, Fb, LinkedIn, Microsoft, Twitter accounts
Towards the tip of my follow-up interview with Schafer and VCPI’s Christianson, I shared Holden’s record of web sites for which the attackers had apparently stolen inner firm credentials. At that time, Christianson abruptly ended the interview and bought off the road, saying she had private issues to take care of. Schafer thanked me for sharing the record, noting that it regarded like VCPI most likely now had a “few extra notifications to do.”
Ethical of the story: Corporations that have a ransomware assault — or for that matter any sort of equally invasive malware infestation — ought to assume that every one credentials saved wherever on the native community (together with these saved inside Net browsers and password managers) are compromised and must be modified.
Out of an abundance of warning, this course of must be executed from a pristine (ideally non-Home windows-based) system that doesn’t reside inside the community compromised by the attackers. As well as, full use must be fabricated from the strongest methodology obtainable for securing these passwords with multi-factor authentication.
*** It is a Safety Bloggers Community syndicated weblog from Krebs on Safety authored by BrianKrebs. Learn the unique submit at: https://krebsonsecurity.com/2020/01/the-hidden-cost-of-ransomware-wholesale-password-theft/
[ad_2]
Source link