[ad_1]
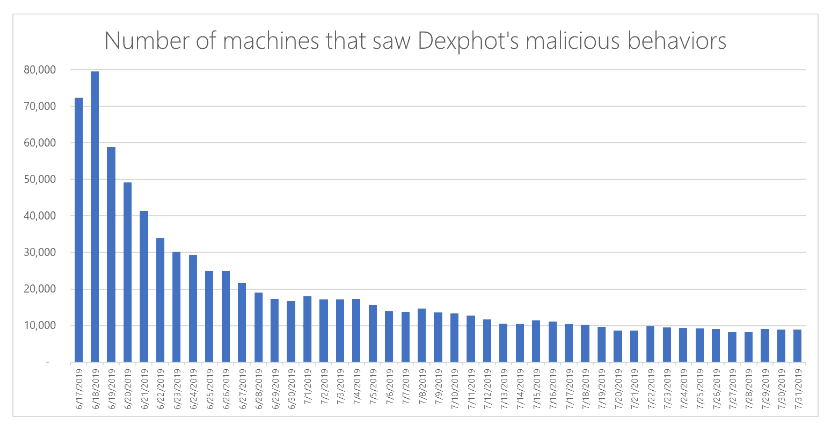
As we speak, Microsoft detailed new malware pressure has been infecting Home windows computer systems through Dexphot since October 2018. Its peak was in June when the variety of contaminated computer systems was over 80.000.
Dexphot is a sophisticated malware, which is a software for hackers to mine cryptocurrencies and generates income for the attackers. Thus, it doesn’t steal consumer information.
This malware began from harming the content material of two professional processes – svchost.exe and nslookup.exe. Then, they used duties to make the sufferer be contaminated as soon as each 90 minutes. Additional, they successfully used polymorphism, which makes all programs very sophisticated.
Amongst all duties, essentially the most eye-catching factor is “polymorphism camouflage”, which is ready to change footprint and file names on the pc each 20-30 minutes. Thus, it makes Home windows computer systems extra weak when it comes to cybercriminal elements.
Dexphot is supplied with 5 recordsdata: an installer with 2 URLs, a loader DRL, and an encrypted information file, which incorporates three further recordsdata. Since all processes are professional, aside from the set up course of, restoration may be very tough. Furthermore, Dexphot used to cope with computer systems that had been beforehand contaminated by different malware, i.e it makes the issue extra complicated.
It’s predicted that Dexphot will have the ability to hurt another vital processes comparable to svchost.exe, tracert.exe, and setup.exe. Moreover, it will additionally make use of a way known as “dwelling off the land” to abuse professional Home windows processes and to execute malicious code, somewhat than run its personal processes. In keeping with Microsoft, Dexphot was ready to make use of unzip.exe, powershel.exe and so forth for its ‘functions’.
Though Dexphot has sturdy persistence mechanisms, no malware stays unrevealed ceaselessly. And on account of efforts and related insurance policies of Microsoft, the variety of assaults is repeatedly declining.
[ad_2]
Source link